Issue Date:August 20, 2025
To implement sustainable development and protect the Company’s confidential information and customer privacy, the Company established the “Information Security Management Committee” in 2012. This committee is responsible for implementing information security policies and establishing communication mechanisms to effectively prevent data theft, tampering, loss, or leakage. In addition to ensuring the confidentiality, integrity, and availability of information, the Company also complies with the ISO 27001 standard and other relevant information security regulations.
Information Security Management Committee
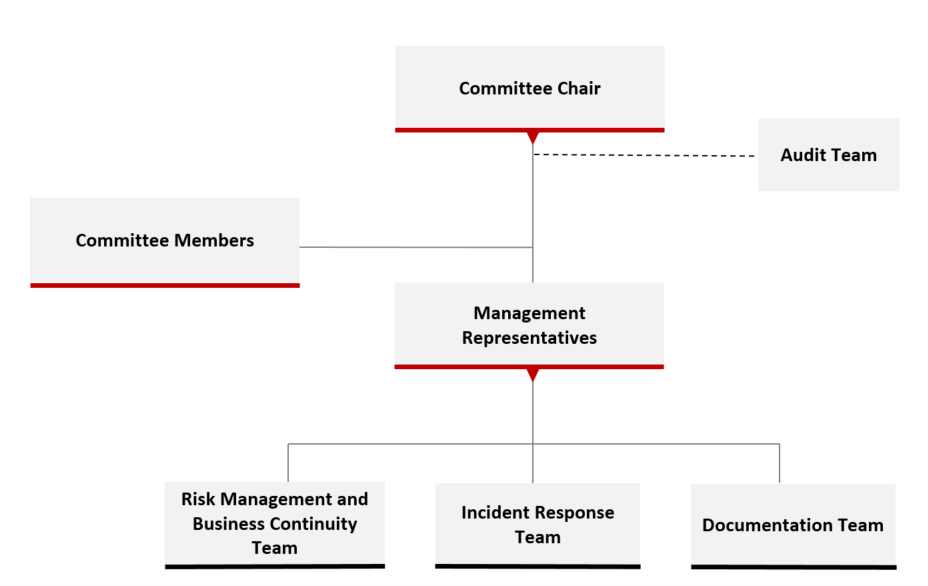
The Company established the “Information Security Management Committee” in December 2012. The committee is responsible for reviewing information security governance policies, overseeing the implementation of information security management, establishing a comprehensive information security protection mechanism, enhancing employee awareness of information security, and conducting regular assessments of information security risks. Since 2020, the committee has reported its implementation status to the Board of Directors annually.
The committee is chaired by the Vice President or a person appointed by the Company’s President (hereinafter referred to as the Committee Chair). Members include first-level supervisors from each department who assist the Committee Chair in managing operations and maintenance. Each department’s management representative is responsible for supervising and managing committee-related tasks within their respective units. Additionally, the committee has established a Risk Management and Business Continuity Team, an Incident Response Team, and a Documentation Team. (For the organizational structure, please refer to the bottom diagram.)
Information Security Policy
The Company formulates the following information security policies based on ISO 27001 and NIST standards, and in accordance with internal management needs:
- Each unit within the Information Management Center maintains an inventory of relevant information assets and designates the asset owners. Risk assessments are conducted based on the classification of assets. For risks exceeding acceptable levels, appropriate risk management measures are implemented to mitigate risks effectively, and various control measures are continuously enforced.
- Personnel must undergo necessary assessments before employment and sign relevant operational regulation documents. Upon transfer or resignation, all assigned information assets must be returned. Both new and current employees are required to participate in information security training to enhance awareness and understanding of information protection.
- Access control protocols and rules for carrying items in and out of the company buildings and information security control zones must be strictly followed.
- Employees are strictly prohibited from privately installing network equipment that connects the external network to the Company’s internal network. Firewalls, demilitarized zones (DMZ), and necessary security facilities must be established for both internal and external networks. Critical equipment should have proper backup or monitoring mechanisms to maintain availability. Employees' personal computers must have antivirus software installed and virus definitions regularly updated. The use of unauthorized software is prohibited.
- Employees are responsible for safeguarding and properly using their individual accounts, passwords, and access privileges. System administrators must regularly review and verify user permissions. Data from critical systems must be backed up regularly, and recovery tests must be conducted.
- Security controls should be considered in the initial phase of system development. For outsourced development, enhanced controls and contractual information security requirements must be enforced.
- If an employee encounters an information security incident, it must be reported immediately and handled according to the Information Security Incident Handling Procedure to prevent escalation. Cooperation with responsible departments is required to resolve the issue.
- Employees must follow proper review and verification procedures in daily operations to maintain data accuracy. Supervisors are responsible for ensuring compliance with information security policies and strengthening employees’ awareness of information security and relevant regulations.
- The Company reviews its information security policies regularly to respond to changes in government regulations, technologies, and business needs. The Information Security Management Committee adjusts objectives accordingly to ensure the effectiveness of information security practices.
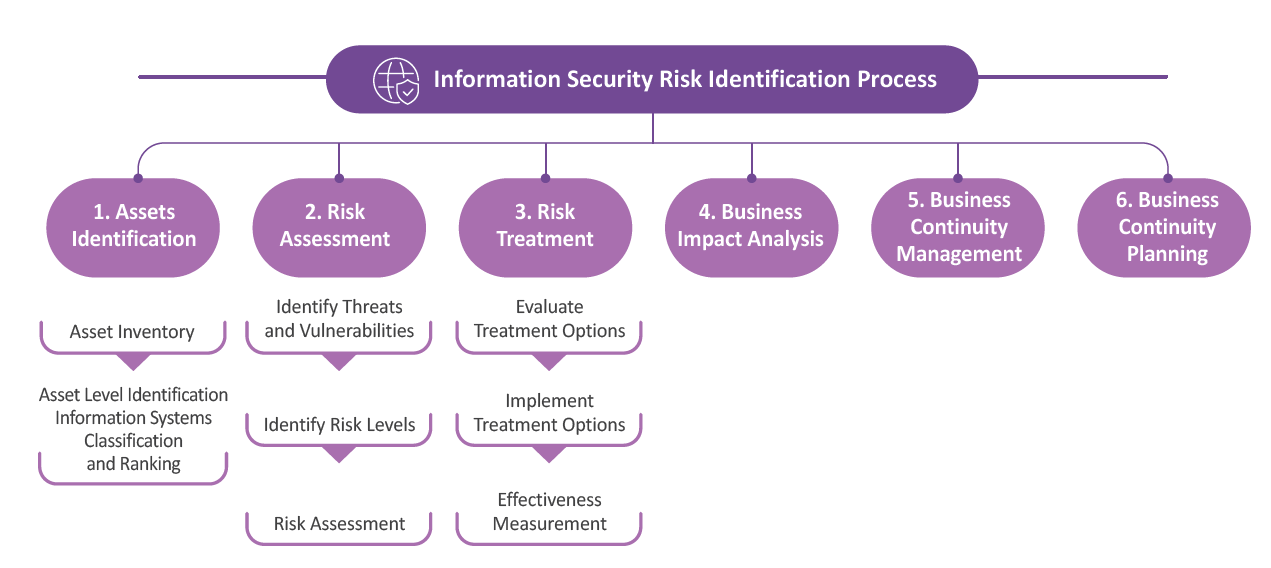
Information Security Risk Identification
- Policy:Based on the 14 control objectives and 114 control measures of ISO 27001, Coretronic strengthens information security across six key areas: network security, host security, application system security, equipment security, operations analysis, and information security management. The risk mitigation process is systematized and data-driven, establishing a defense-in-depth architecture to enhance overall information security strength.
- Annual Targets:Annual information security management targets are set, with evaluation metrics tailored to each target. Using data-based indicators and standardized procedures, the Company identifies non-compliant or high-risk issues, proposes improvement measures, and includes them in follow-up tracking.
- Vulnerability Scanning:To respond to the rapidly evolving methods of cyberattacks, the Company regularly conducts vulnerability scans on systems that provide services. All detected vulnerabilities are fully resolved within three months.
Information Security Education and Training
- Information Security Training: A total of 11 information security-related courses were offered, including “Welcome Aboard: Information Security for New Employees”, “Email-Based Social Engineering Attacks”, “Phishing and Impersonation Scams”, “Cybersecurity Identification and Protection Essentials”, “Network Information Security and Computer Usage Guidelines”, and “Corporate Information Security Training”, with a total of 2,756 participations.
- Security Announcements: Information security awareness announcements were issued periodically to remind employees of relevant risks and help prevent recurrence that could lead to operational losses for the Company. In 2024, a total of 8 announcements were made.
- Social Engineering Drills: Two email-based social engineering simulation drills were conducted for all employees across the group.
Information Security Measures
- Established a defense-in-depth information security architecture to enhance protection across six major aspects: network security, host security, application system security, equipment security, operations analysis, and information security management.
- Strengthened the information security protection architecture by upgrading the forensic analysis platform to ensure no vulnerabilities exist in the defense system.
- Maintained real-time synchronization with international threat intelligence centers, continuously updated threat intelligence, and utilized a proactive alert analysis engine to block malicious connections and actively detect suspicious behavior effectively. This is further supported by information security experts conducting forensic investigations to enhance defense capabilities against hackers.
- In response to updates of externally provided service systems, since 2020, the Company has conducted at least one platform vulnerability scan and one social engineering drill each year.
